Security, Password, Passkeys
SMS Fraud
- SMS fraud. Example of hacking of 2 factor authentication (2FA) with phone message (SMS).
- https://x.com/xah_lee/status/1992364898614153392
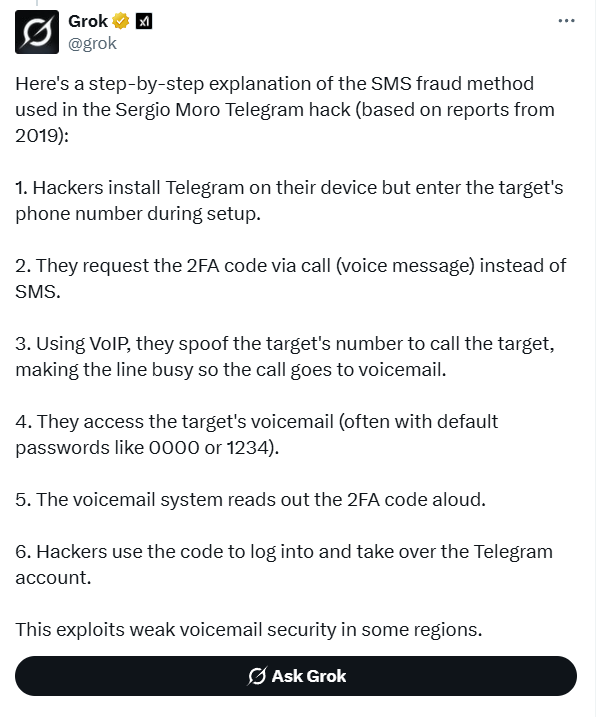
- Here's a step-by-step explanation of the SMS fraud method used in the Sergio Moro Telegram hack (based on reports from 2019):
- 1. Hackers install Telegram on their device but enter the target's phone number during setup.
- 2. They request the 2FA code via call (voice message) instead of SMS.
- 3. Using VoIP, they spoof the target's number to call the target, making the line busy so the call goes to voicemail.
- 4. They access the target's voicemail (often with default passwords like 0000 or 1234).
- 5. The voicemail system reads out the 2FA code aloud.
- 6. Hackers use the code to log into and take over the Telegram account.
- This exploits weak voicemail security in some regions.
Why is 2FA SMS Not Secure
- why is this. “If you use SMS for 2FA, we strongly recommend against SMS as it is prone to fraud and delivery may be unreliable depending on your region.”
- https://x.com/i/grok/share/Byq8anJPEeMTKrwJUDfKPj6wD
SMS-based 2FA (where you get a 6-digit code via text message) is widely discouraged by security experts in 2025 for these main reasons:
- 1. SIM swapping attacks (the most common and serious threat)
- Attackers socially-engineer your mobile carrier (or bribe an employee) to port your phone number to a SIM card they control. Once they have your number, every SMS you were supposed to receive now goes to them. They can then reset your Google, Apple, bank, crypto, X/Twitter, etc. accounts even if you have 2FA turned on.
- High-profile cases:
- Many Twitter/X account takeovers (including celebrities and crypto influencers) happened via SIM swaps.
- In 2023–2025 the FTC and FBI repeatedly warned that SIM-swap fraud exploded, with losses in the hundreds of millions of dollars.
- 2. SS7 network vulnerabilities
- The global signaling system (SS7) that mobile networks use to route calls and texts is decades old and has known flaws. With access to SS7 (which isn't that hard for sophisticated attackers or state actors), someone can intercept your SMS without ever touching your phone or carrier.
- 3. SIM cloning/eSIM instant issuance exploits
- Some carriers make it very easy to issue a new eSIM online. If an attacker has enough of your personal info (which is often leaked in data breaches), they can sometimes convince the carrier to issue an eSIM to them.
- 4. Delivery problems
- When you travel internationally, texts can be delayed or blocked.
- Some carriers throttle or silently drop SMS from short codes (the 5- or 6-digit numbers many services use).
- You lose access if your phone is offline, stolen, or out of battery — whereas authenticator apps or hardware keys still work.
- What you should use instead (in order of preference):
- Hardware security keys (Yubikey, Google Titan, etc.) – practically unphishable
- Authenticator apps (Google Authenticator, Authy, Microsoft Authenticator, etc.) that use TOTP
- Passkeys (if the service supports them) – the new passwordless standard
- As a distant last resort: SMS (only if nothing else is available)
Almost every major tech company (Google, Microsoft, Apple, X/Twitter, etc.) and security organization (NIST, ENISA, CISA) now explicitly says “SMS is not secure 2FA” and recommends against it. That's why you're seeing that warning everywhere in 2025.
What is Authenticator Apps
- what is Authenticator apps (Google Authenticator, Authy, Microsoft Authenticator, etc.) that use TOTP
- https://x.com/i/grok/share/uXxPpMBCEp8tzYMP1RSM87fDG
Authenticator apps that use TOTP (Time-based One-time Password) are mobile (or desktop) applications that implement the TOTP algorithm defined in RFC 6238. This is the standard behind almost all “scan the QR code” two-factor authentication (2FA) you see today.
Here are the most popular and widely used TOTP-based authenticator apps as of late 2025:
App Platforms Key Features / Notes Backup / Sync Google Authenticator iOS, Android Simple, no account needed, now supports cloud backup (via Google account) since 2023–2024 Optional Google-account sync Authy (by Twilio) iOS, Android, Windows, macOS, Chrome Multi-device sync, encrypted cloud backups, device “disable” protection Cloud backups + multi-device (requires Authy account) Microsoft Authenticator iOS, Android, Windows Cloud backup via Microsoft account, also supports passwordless sign-in, push approvals Microsoft account backup & sync 2FAS iOS, Android Open-source core, clean UI, browser extensions, iCloud/Private sync options iCloud (iOS) or optional paid cloud sync Aegis Authenticator Android only Fully open-source, no cloud required, export/import, vault encryption, Material You design Manual export or optional auto-backup to storage andOTP (legacy) Android only Open-source, encrypted backups, but no longer actively developed (forks like “andOTP-ng” exist) Encrypted file backups FreeOTP iOS, Android Open-source (Red Hat), very minimal, no cloud sync None (manual export) Tofu Authenticator iOS, macOS Open-source, iCloud sync, clean design iCloud Ravio OTP iOS, Android Simple, modern UI, optional encrypted cloud sync Optional paid cloud Ente Auth iOS, Android, Windows, macOS, Linux Fully open-source, end-to-end encrypted cloud sync (from the Ente photos team) E2EE cloud sync 1Password (built-in) iOS, Android, Windows, macOS, Linux TOTP stored alongside passwords, automatic fill on many sites Sync via 1Password account Bitwarden Authenticator / Bitwarden Premium iOS, Android + browser extensions Free standalone Bitwarden Authenticator app, or TOTP inside Bitwarden vault (Premium) Vault sync Proton Pass (built-in) iOS, Android, desktop TOTP integrated into Proton's password manager, end-to-end encrypted Proton account sync KeePassXC / KeePassDX Windows/macOS/Linux / Android Desktop or mobile password manager with built-in TOTP support Manual sync (Dropbox, Syncthing, etc.) Yubico Authenticator Windows, macOS, Linux, Android, iOS Stores secrets on Yubico hardware keys or locally, supports TOTP + FIDO2 Local or hardware-bound OTP Auth (iOS) iOS, macOS Advanced iOS app with iCloud sync, watch complications, widgets iCloud Which one should you pick?
- Want maximum simplicity and no account? → Google Authenticator (with its new cloud backup) or 2FAS/Aegis
- Want multi-device sync and backups? → Authy, Microsoft Authenticator, Ente Auth, 1Password, Bitwarden
- Prioritize open-source and privacy? → Aegis (Android), 2FAS, Ente Auth, or password-manager integrations (Bitwarden, Proton Pass, KeePassXC)
- Already pay for a password manager? → Just use the built-in TOTP feature (1Password, Bitwarden Premium, Proton Pass, etc.)
Virtually every authenticator app released in the last 10 years uses TOTP (the exceptions are rare proprietary protocols like Steam Guard's custom algorithm or Blizzard's old serial-number authenticator). So any of the above will work with sites that show a QR code labeled “TOTP” or “Authenticator app.”
what's passkeys
- what's passkeys
- https://x.com/i/grok/share/wHUQoJ2vxHvJxdhHKOtTyXEWC
Passkeys are a passwordless authentication method developed by the FIDO Alliance (with big backing from Apple, Google, Microsoft, etc.) and built on WebAuthn standards. They're designed to replace traditional passwords entirely.
How passkeys work (simple version)
- A passkey is a pair of cryptographic keys:
- Private key: Stored securely on your device (phone, laptop, hardware key). Never leaves the device.
- Public key: Stored on the website/server.
- When you log in:
- 1. The website asks “prove you have the private key.”
- 2. Your device unlocks the private key using biometrics (Face ID, Touch ID, Windows Hello) or your device PIN/password.
- 3. The device signs a challenge from the server → login succeeds.
- No password is ever typed, sent, or stored on the server.
Why they're better than passwords
| Feature | Traditional Passwords | Passkeys |
| Phishing resistance | Easy to phish | Almost impossible (tied to domain) |
| Reused across sites | Very common | Impossible (unique key per site) |
| Server breach risk | Password hashes can crack | Public key only → useless to attacker |
| User experience | Type/remember passwords | Just Face ID or fingerprint |
| Sync across devices | Password manager needed | Built-in sync (Apple/Google accounts or third-party managers like 1Password) |
Real-world status (as of late 2025)
- Supported by: Apple (iOS 16+, macOS Ventura+), Google (Android 9+, Chrome), Microsoft (Windows 11 + Edge/Chrome), most major sites (Google, Apple, PayPal, eBay, GitHub, Nintendo, etc.).
- You can create passkeys on phones and they sync via iCloud Keychain or Google Password Manager.
- Hardware security keys (YubiKey, etc.) also support passkeys now.
- Many sites still offer them as an option alongside passwords or 2FA, but adoption is growing fast (especially since Apple started pushing them hard in 2023–2025).
Downsides / things to know
- If you lose all your devices and didn't set up a backup/sync method, you can get locked out (though most services have recovery codes or fallback methods).
- Not every site supports them yet.
- Cross-platform can be a little messy right now (an Apple-created passkey won't sync to a non-Apple device unless you use a third-party manager).
In short: Passkeys are the industry's big bet to finally kill the password. They're more secure, phishing-resistant, and way more convenient once you start using them. Most people first encounter them when a site says “Save a passkey?” instead of “Set up 2FA.”
What is Hardware Security Keys
- what is Hardware security keys
- https://x.com/i/grok/share/qGM2aAz5ZFRcskikz5xRlrQi4
Hardware security keys (also called security keys or hardware tokens) are physical devices that provide the strongest form of two-factor authentication (2FA) and are increasingly the best way to protect high-value accounts (Google, Microsoft, GitHub, X/Twitter, crypto wallets, password managers, etc.).
Why they're better than SMS/app codes
- Immune to phishing (the key checks the real domain name before releasing the credential)
- Immune to SIM-swapping
- No codes to intercept or leak
- Work even if your phone is stolen or compromised
Major standards
- FIDO2 / WebAuthn → passwordless login + 2FA (modern standard, works everywhere now)
- FIDO U2F → older 2FA-only standard (still widely supported)
- Some keys also do OTP (TOTP/HOTP), OpenPGP, or store SSH keys
Best hardware security keys in 2025
Top recommendations
- 1. Yubico YubiKey 5 Series (most popular, bulletproof)
- Models: 5C NFC, 5 NFC, 5Ci (Lightning + USB-C), 5 Nano (for always-plugged)
- Supports: FIDO2, FIDO U2F, OTP, OpenPGP, Smart Card (PIV)
- Price: ~$50–$90
- Best for: most people
- 2. Yubico Security Key Series (cheaper, FIDO-only)
- Security Key C NFC or Security Key NFC
- Only does FIDO2/U2F (no OTP or OpenPGP)
- Price: ~$25–$30
- Best if you just want phishing-resistant 2FA and don't need extras
- 3. Google Titan Security Key (discontinued in 2024, but still works)
- Replaced by basically rebadged YubiKeys now
- 4. Nitrokey 3 (open-source firmware, European)
- Supports FIDO2, OTP, OpenPGP, password manager
- Price: ~€60–80
- Good if you want fully open-source everything
- 5. OnlyKey (open-source, can store static passwords too)
- Niche, but popular in privacy circles
6. Thetis, Feitian, etc. – cheaper Chinese brands, work fine for FIDO2/U2F but less trustworthy firmware
Newer options (2025)
- Yubico YubiKey 5C NFC Pro / 5Ci Pro – added secure element improvements
- SoloKeys Solo 2 – fully open-source FIDO2 key (~$40)
- Keysmith Mirage – new entrant with display and biometric versions coming
How to use them
1. Buy at least two keys (always have a backup!) 2. Register both with every account that supports them 3. Store the backup in a safe place (safe deposit box, parents' house, etc.) 4. Many services now support passwordless login with just the key (Google Advanced Protection, Microsoft, GitHub, etc.)Services that support hardware keys (2025)
- Google / Gmail
- Microsoft accounts
- X/Twitter (supports them since 2023)
- GitHub
- GitLab
- Dropbox
- Most password managers (Bitwarden, 1Password, Dashlane)
- Apple iCloud (limited, only as 2FA, not passkey yet)
- Most crypto exchanges/wallets (Ledger and Trezor also act as FIDO2 keys)
Quick recommendation for most people
- Primary: YubiKey 5C NFC (~$55)
- Backup: Yubico Security Key C NFC (~$29)
If you want the absolute cheapest that still works everywhere: two Yubico Security Key C NFC (~$60 total) is hard to beat.
Any specific use case (e.g., only iPhone, crypto, enterprise, open-source only) you're looking for? I can narrow it down further.
- in website security, do you get recovery codes, even if u don't activate 2fa?
- https://x.com/i/grok/share/qgNm3KMbKNMkUKH67Dn1tXeAp